Now that OS X El Capitan or version 11 is out, I'll do a refresh for the USB installation instructions.
The thing is ... the upgrade free, but it's big. The amount of downloading needed is easily 6+ GiB. I have 3 Macs to update and I don't want to download the huge package on all of them. So, let's figure out something smarter.
Step 0: Prerequisites
You'll need a bootable USB-stick with capacity of 8 GiB or more. All sticks should boot, but I have encountered some that didn't manage that.
USB-booting a Mac is trickier than a PC. The knowledge base article HT1948 states:
Intel-based Macs support starting from an external USB storage device's volume that:
- Has been formatted with a GUID partition type
- Contains an installation of Mac OS X 10.4.5 or later, or Mac OS X 10.5 or later, which is compatible with (or shipped with) the Mac that the USB device is connected to. Note: You should not use a version of Mac OS X that is earlier ("older") than the version your Mac shipped with.
So, if you just bought an USB-stick, the chances are, that it is MBR-partitioned FAT32. That's my experience of getting new ones. They are incompatible at their current state for USB-booting a Mac. Not to worry, that can be fixed!
If you happen to have a ready-made stick for any previous OS X version, that obviously can be loaded with new installer. You can even skip couple of things during the process as you don't have to reformat the stick.
Step 1: Go download
In your Apple menu (the top left apple-shaped thing at every program's menu), go for Software Update. An alternate is to click the App Store link:
![]()
Both options land you on the App Store main screen showing you something like this:
![]()
Click the image saying Free Upgrade (free as in beer):
![]()
Your Apple ID credentials are required for this free package. They'll keep track of who downloaded and what.
This is the part you'll wait for the download to complete:
![]()
When it's all on your machine, the installer will automatically kick in.
Step 2: Go USB
Now that you have the thing in your drive, don't proceed with the upgrade.
When you reach this screen:
![]()
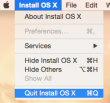
do not proceed! You can quit the installer, if you want:
![]()
It won't delete the files from your drive. It is also possible to continue installing on that Mac, but don't do it yet. Take a copy of the files first.
Take at least a 8 GiB USB-storage. 4 won't do it, but any larger will. In my case, the USB-stick appeared as /dev/disk3. That may vary on your system. Also it is possible to use some GUI-tools on OS X to format your drives, but as a Linux-nerd I don't know about them.
It is very likely, that the disk is mounted and will display an icon on your desktop, and will appear on your Finder. The diskutil will unmount it automatically on partition, but I wanted to make sure and did:
# sudo diskutil umount /Volumes/MyUSBdrive
Next step is to make sure, the stick is in a Mac-format (this needs to be run as root, that's what the sudo is for). This will partition and format the entire stick into Mac-use:
# sudo /bin/bash
root# diskutil partitionDisk /dev/disk3 1 GPT jhfs+ "OS X El Capitan" 0b
It will say something like this as a result:
Started partitioning on disk3
Unmounting disk
Creating the partition map
Waiting for the disks to reappear
Formatting disk3s2 as Mac OS Extended (Journaled) with name OS X El Capitan
Initialized /dev/rdisk3s2 as a 7 GB case-insensitive HFS Plus volume with a 8192k journal
Mounting disk
Finished partitioning on disk3
/dev/disk3
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *8.0 GB disk3
1: EFI EFI 209.7 MB disk3s1
2: Apple_HFS OS X El Capitan 7.7 GB disk3s2
Next thing is to confirm, that the volume with given name will be mounted:
root# ls -l /Volumes/
total 40
lrwxr-xr-x 1 root admin 1 Aug 29 12:24 Macintosh HD -> /
drwxrwxr-x 7 root wheel 306 Oct 10 12:41 OS X El Capitan
If it does, you're ready to go. Copy the thing into it:
root# cd /Applications/Install\ OS\ X\ El\ Capitan.app/Contents/Resources/
root# ./createinstallmedia --volume /Volumes/OS\ X\ El\ Capitan/ \
--applicationpath /Applications/Install\ OS\ X\ El\ Capitan.app/ \
--nointeraction
It will result in a lengthy process saying:
Erasing Disk: 0%... 10%... 20%... 30%...100%...
Copying installer files to disk...
Copy complete.
Making disk bootable...
Copying boot files...
Copy complete.
Done.
Step 3: Go update
Your stick is ready. This is the part you will be replicating to any of your Macs you want to upgrade.
Reboot the Mac and make sure to boot from the USB. This can be achieved by pressing down option-key during boot:
![]()
![]()
The official Apple instruction at knowlegebase article HT1948 states:
To start from a USB storage device that meets the above requirements:
- connect the device
- restart
- immediately press and hold the Option key to access Startup Manager
If you successfully followed the steps, you will end up in Mac boot manager:
![]()
In that, you pretty much select the drive you want to boot from. In this particular case, making a choice for the recently prepared USB-stick will be a good one. Click the orange "Install OS X El Capitan". Both the gray HD and the network selection are there to confuse you. Ignore them and double click the USB-drive.
Most steps in this upgrade will include lot of waiting. Make sure that you have reserved couple of hours for the upgrade. Screens like this will become familiar to you:
![]()
Most time estimates are wild guesses. A 9 minute wait in reality is something like 45 minutes. Eventually the USB-stick finishes booting, and you will end up in a screen saying "To set up the installation of OS X, click Continue". Most screens will refer your upgrade as an install. It is nerve-wrecking thing, because you don't know if it is going to wipe your settings and data, or do a nice upgrade what you'd be expecting. My experience is, that it will upgrade nicely, but it won't say it properly.
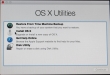
Then there is a license screen which you must agree to continue. Then land on OS X Utilities. One thing you can do with a bootable stick is to upgrade or install an OS X:
![]()
When you select to go for upgrade or install, there is a welcome to OS X El Capitan screen. Click Continue. Yet another license screen appears. Click Agree and for the confirmation dialog: I have read and agree to the terms of the software license agreement, Agree. Select the install/upgrade destination as the one having a hard drive icon Macintosh HD (typical installations have that), then click Install. As the first thing, the installer/upgrader will prepare for the operation and then go for the real thing:
![]()
![]()
This is the most time-consuming part. After a minute or so, there will be an not-so-accurate estimate of time remaining for the preparation. When it has run its course, the actual installer will start. So if the screen says 1 minute left, do not believe it for a second. In my iMac, one cup of coffee doesn't do it. You can easily cook and eat a meal and then have the coffee while the installer/upgrader runs. Especially the final phase saying "About a second remaining" will take ages. My hardware isn't especially old or slow, but ... the process is.
Step 4: Finishing touches
After you've done your waiting. A reboot will result. At this point you'll need to login into your precious upgraded Mac with your local user account.
![]()
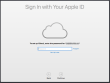
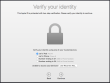
On successful login, you will end up in the OOBE (or out-of-box experience). Apple makes an effort to not allow stolen hardware to be used and they pretty much require you to login to Apple ID during install:
![]()
Since I have a 2-factor authentication enabled for my Apple ID, a 2FA-screen will appear during the process:
![]()
There are steps about sending your usage data to Apple. Then yet another license screen which you have to agree twice. First on the bottom screen and then on the pop-up that will appear. So if you want to complain later, they'll just say "but you did agree to our terms and conditions". It will look like this:
![]()
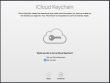
The last question you'll need to answer is about setting up iCloud Keychain. I choose not to share my passwords into any cloud services, but at this point you'll have the option to enable Keychain:
![]()
Little bit of setting up ... this one won't take long. And then you're pretty much done. Finally your upgrade is ready!
![]()
Step 5: Done!
Login for the first time:
![]()
One of the first things I did, was eject my USB-stick (there were couple other Macs to be updated, too):
![]()
At this point, you can continue using your precious Mac.
Aftermath
I updated anyway, as a nerd I like the latest stuff running on my computers. I should yield less problems and there needs to be some progress. I find myself stating the same thing in couple of my blog posts, "it wasn't worth it, but I did it anyway". With computers, it never will result any good to stand still and ignore future.
 A small dialog will open. Select More information:
A small dialog will open. Select More information:
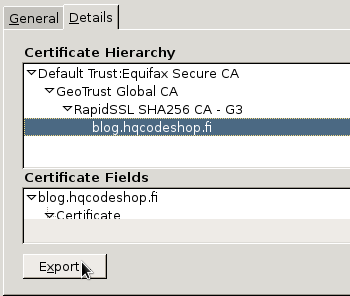































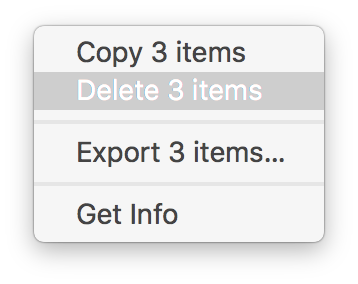 And that solved it! Simply letting the weird ones go made all my websites work again.
And that solved it! Simply letting the weird ones go made all my websites work again.